QoS Usage and Applications
Planning and Implementing Quality of Service Policies
The process of creating Quality of Service (QoS) policies can be broken down into three steps:
1. Identify network traffic, baseline behavior, and service-level requirements
2. Divide traffic into application classes
3. Define QoS policies for the application class to meet service-level requirements
Identify network traffic, baseline behavior, and service-level requirements
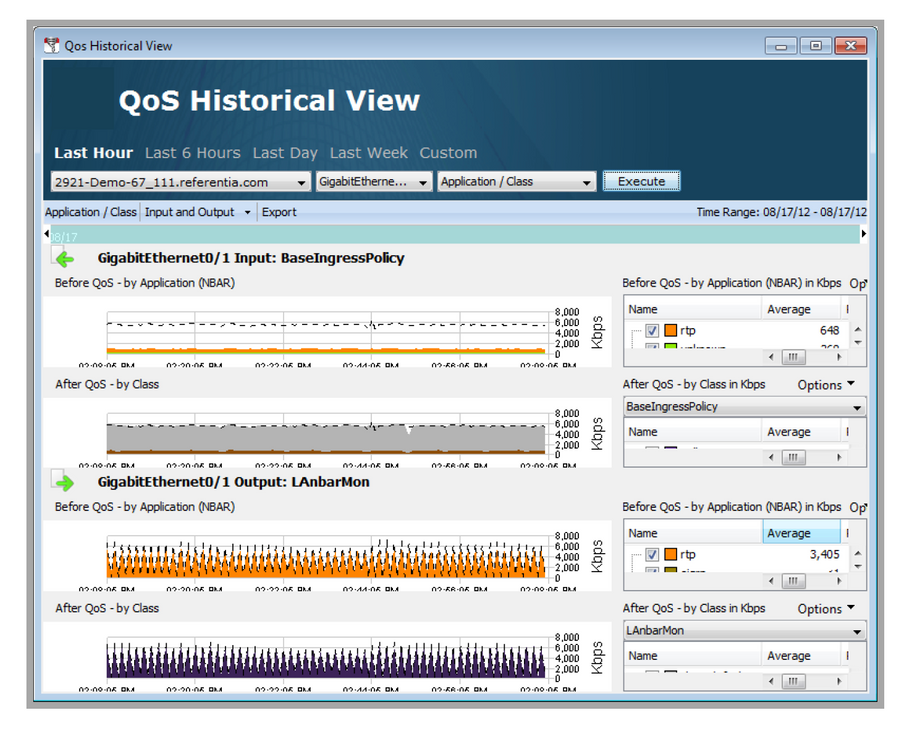
Perform a network audit using the QoS historical views to identify traffic types and volumes. LiveNX provides this functionality through the monitoring graphs. Then, perform a business review on the priorities and specific requirements for the discovered traffic.
Divide traffic into application classes
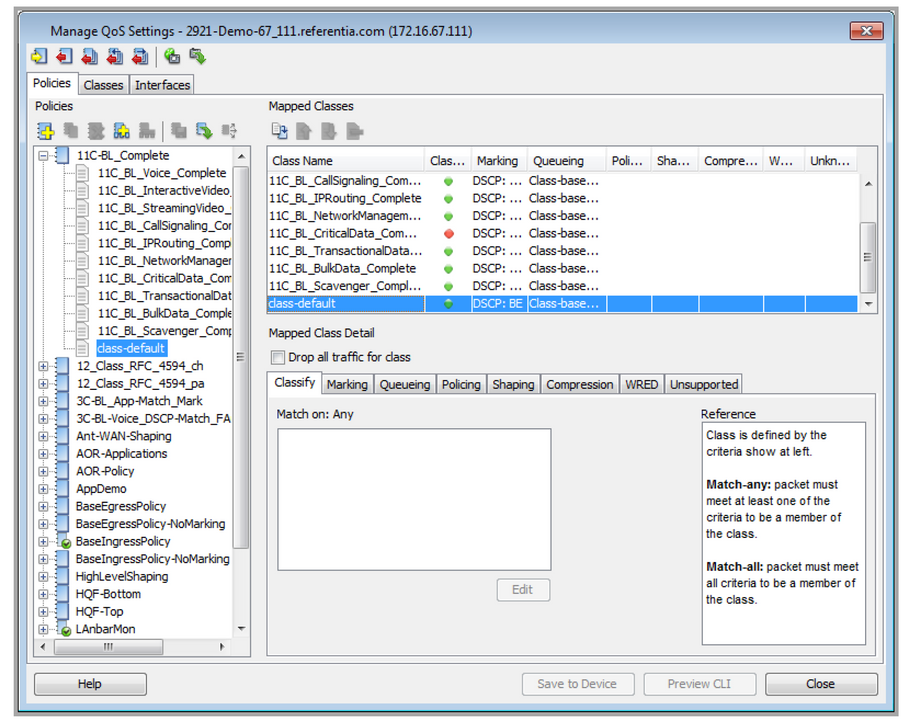
Traffic can be divided into classes based on the identified traffic and the business requirements. The Cisco baseline model, which consists of 11 classes, is designed to provide granularity for various class types with different service requirements. Each type of class may have unique QoS requirements that must be configured and monitored. For initial QoS deployment, a smaller 4- or 5-class model can be used to simplify the process. The model can easily be expanded over time as additional applications and requirements arise.
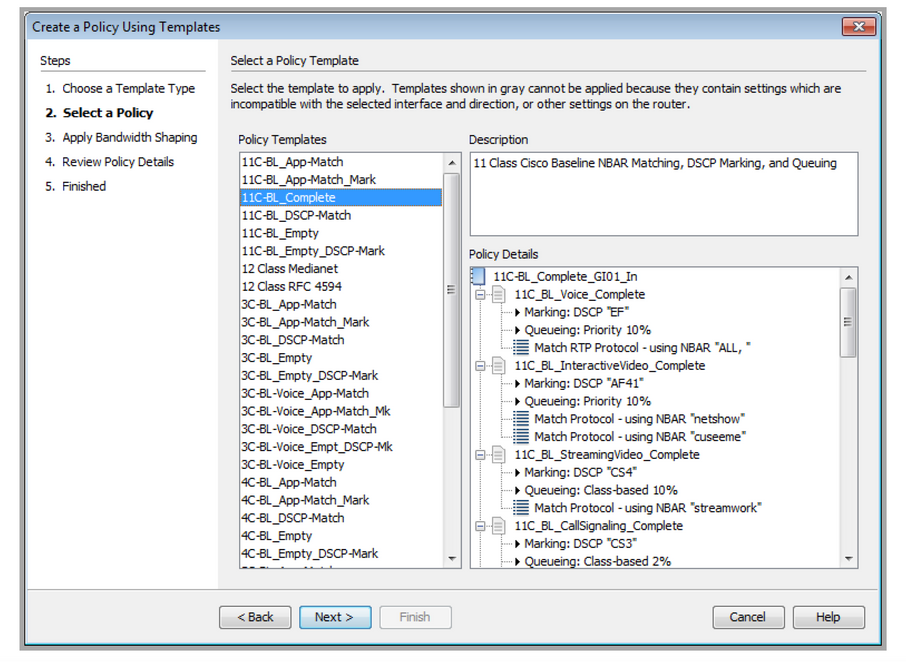
Define QoS policies for the application class to meet service-level requirements
QoS policies should be designed from high-level requirements to meet specific objectives. Once the requirements are understood, they can be translated to QoS best practices for the various application types.
• Some best practices include using DSCP markings and marking the packets as close to the source of the traffic as possible.
• Recreational or Scavenger traffic should be policed as close to the source as possible to prevent unnecessary bandwidth usage ifit exceeds a certain threshold.
• Critical applications should be ensured through class definitions to meet service level agreements.
• A majority of the traffic will be classified as default, so enough bandwidth should be provided to support this type of traffic.
• Real-time traffic should use priority queues and be assigned adequate bandwidth. However, you should limit the overall priorityqueue to 33% of the available bandwidth to prevent starving other application traffic.
• The total bandwidth allocation for classes other than default should not exceed 75% of a link’s capacity, to account for Layer 2overhead and Best Effort traffic.